Step 1: Install Kamal
First, we need to install Rails and Kamal. Assuming you have Ruby installation in your local machine, run:Step 2: Create a Simple Rails App
Next, create a basic Rails app using PostgreSQL as the database and Tailwind CSS for the frontend, and generate a scaffold:Step 3: Configure Routes
Set the root route to serve the/posts endpoint by updating config/routes.rb:
Step 4: Set Up Docker Registry
Now, we need to set up a dockerhub repository to store and fetch our images. For that, you need to create an account at https://hub.docker.com. Once you have the account, please create a new repository named “blog” in the docker hub page and generate a new key at https://app.docker.com/settings/personal-access-tokens and paste it to the .env file as shown below..kamal/secrets to copy the key from the environment:
config/deploy.yml file to make it load from .env, and include your docker registry and the service names in place:
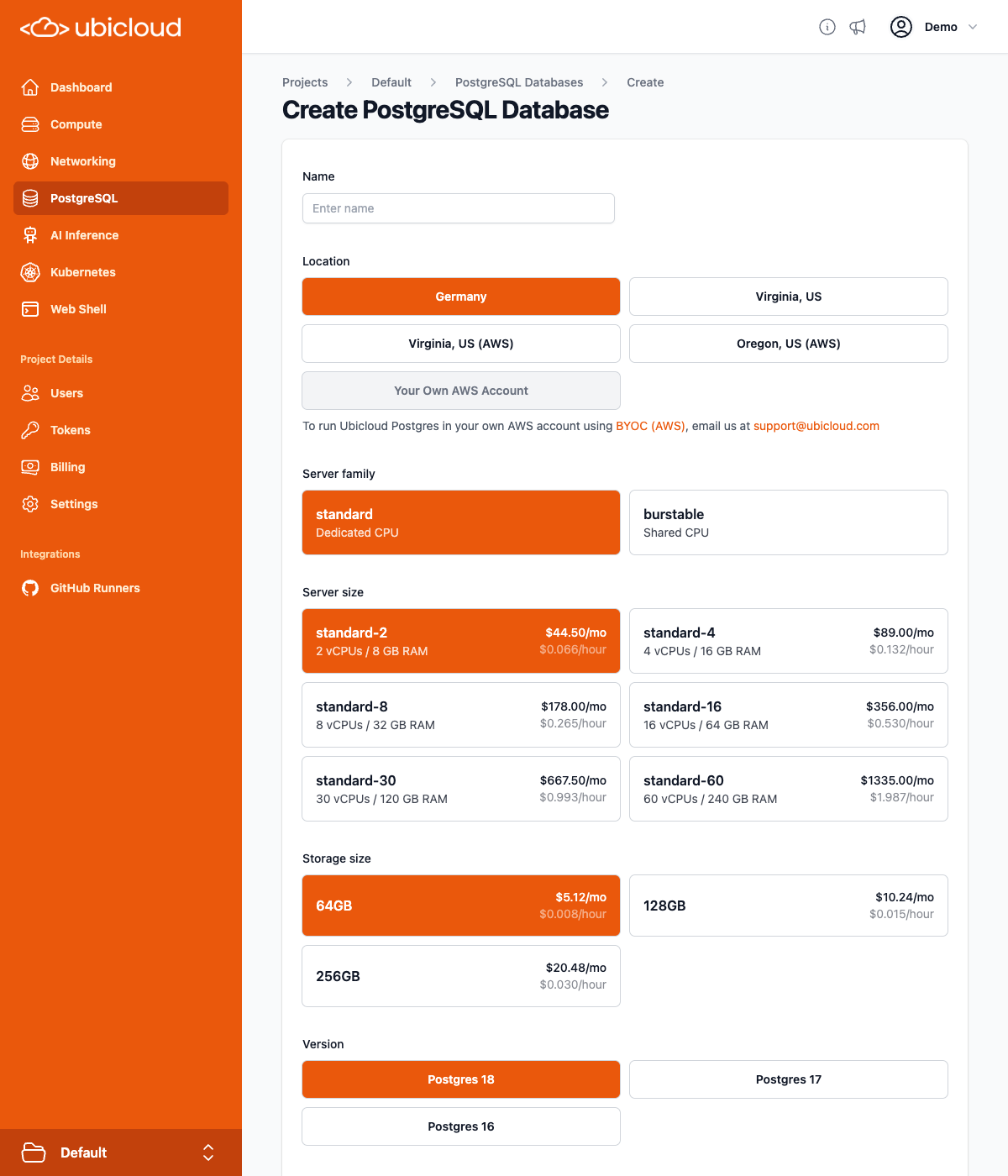
Step 5: Set Up Ubicloud Resources
Create the following resources:-
Virtual Machines (VMs): Create a VM from console.ubicloud.com. When creating the VM, you need to pay attention to three things:
- For the location, pick Germany. Later, we’re going to provision a managed Postgres in the same region.
- Make sure to include an IPv4 address, as Kamal 2 will have deployment issues in IPv6 only environments.
- Change the user from
ubitoroot. We userootbecause Kamal installs Docker and connects to it on the VMs. Usingrootavoids the need to manage users and groups.
-
Managed PostgreSQL Database: Set up a managed PostgreSQL database.
Step 6: Gather Resource Information
After setting up the resources, collect the following information from the Ubicloud Console:- PostgreSQL Connection String: Shown by clicking on the database name on the PostgreSQL page
- Public IP of the VM: Shown in the IP Address column on the Compute page
Step 7: Configure Kamal and Environment Variables
Next, copy the master key fromconfig/master.key and paste it into the .env file:
.env file:
config/deploy.yml:
config/deploy.yml file to set the hostname for the application:
config/deploy.yml to pass the environment variables:
config/database.yml to use the DATABASE_URL environment variable, which will already contain the user, password and the database name: